Encryption Keys
Introduction
Data encryption is a security measure that prevents visibility of documents in the case of unauthorized access or theft. Also called data at rest encryption, the data files are encrypted when they are not being used. This encryption is compliant to HIPAA and other American statutes protecting sensitive information from accidental or wrongful disclosure. In the event they are compromised, such as by theft or unauthorized access (including internal unauthorized access), the files are encrypted, and therefore unreadable. When an authorized user accesses a document (such as through editing or viewing within a client application), the document is decrypted and will be able to be read or edited normally. When the user is done with it, it is returned to its encrypted state.
The enforcement of encryption varies by iManage Work environment. For some environments, encryption is automatic and cannot be turned off. For other environments, encryption is optional, and not enabled by default. In that case, each library must be explicitly enabled for encryption. For specific details, contact your iManage Work system administrator. If the environment does not support data at rest encryption automatically, or explicit library-based encryption is not enabled, documents and emails can still be individually encrypted through the following methods. There is no additional effect if more than one condition applies.
The document class sets HIPAA-compliant encryption to Yes. See Classes / Subclasses for additional details.
A custom field (such as custom1 or custom3) specifies document encryption. See Custom Fields for additional details.
The file type specifies document encryption. See File Types for additional details.
However, operations on this page do not include encryption initiated from the previous three methods. These operations are only for data at rest encryption.
Encryption Overview
Encryption uses an electronic cipher, called an encryption key. Encryption keys are implemented in one of two ways: A system-managed key, or optionally, a Customer Managed Encryption Key (CMEK).
A system-managed key is a built-in encryption key provided by the iManage Work system. This is the default key and no steps are needed to manage it. If encryption is enabled, this key is automatically activated. See the Using the iManage system key section.
Customer Managed Encryption Key enables customers to manage their own encryption keys. Customers control their entire process, from generating the customer supplied encryption key (the source key), to loading the keys into iManage Work, deciding when to use each key, and when to revoke or replace keys. For improved security, this process uses a dual-party CMEK where two separate key stores are required. The dual-party CMEK process requires two customer team members, known as key holders, with each independently storing a copy of the same master key in a Microsoft Azure key vault account. The two key stores are then validated by iManage Work that:
iManage Work has access to each of the two Azure key vault accounts, and
The key in each of the Azure key vaults are identical to each other.
Once validated, that key can be activated for encryption. However, should both keys be revoked, encryption and decryption will be stopped.
Implementing dual-party CMEK in iManage Work follows this process with the customer completing each step:
Create the customer supplied encryption key. This is the source encryption key that will be the basis for the rest of the process. See Creating the customer supplied encryption key.
A copy of the customer supplied encryption key should be stored by the company in escrow. If this key is lost, or the password is lost, all documents encrypted from this key will be unrecoverable. In the same way, if the key is compromised, all documents encrypted from this key could be compromised as well.
The customer supplied encryption key is copied twice. Two people, known as key holders, each receive one of the copies.
Each key holder creates a separate Azure key vault and imports the copy of their customer supplied encryption key. This is known as the key store.
Each key holder provides their Azure key vault domain name system (DNS) name to iManage. This allows the customer to pre-authorize the vaults that are permitted for use. See Registering the Azure key vault domain names with iManage.
Each key holder then provides their key store values to an authorized iManage Control Center system administrator. This administrator must be an NRTADMIN and also have the global Key Management privilege. The iManage Control Center system administrator will create a master key based on the two key stores. See Adding a key.
The customer activates this master key in iManage Control Center, and applies to selected libraries. See Activating a key. Immediately after activation, the library uses that master key for all document encryption and decryption. Documents are always decrypted with the current active key.
The following topics are available:
Creating the customer supplied encryption key
Use this to create the customer supplied encryption key.
Creating the customer supplied encryption key and the key vaults are processes completed outside of iManage Work. As part of the best practices and understanding important aspects of the process, iManage recommends certain guidelines. See Azure Key Vault for more information.
Those procedures use a worksheet, called the Azure Information Worksheet, that for your convenience can be used to record required information for later use in these processes.
Registering the Azure key vault domain names with iManage
Before managing encryption keys within iManage Control Center, the customer's Azure key vault domain names must be registered with the iManage Work system.
Each of the two key holders must contact their designated customer service manager (CSM) or their implementation partner and provide their Azure key vault domain names, also referred to as a DNS name. Use the value recorded on line 1 of the Azure Information Worksheet. These two domain names must be different. For example, key holder 1 might be azurevault1.vault.azure.net, and key holder 2 might be azurevault2.vault.azure.net.
The key holders receive verification from iManage Support that the key vault DNS names have been successfully registered with the iManage Work system before continuing.
Adding the global Key Management privilege
NRTADMINs activate and manage keys. They require the global Key Management privilege to see the Encryption Key menu option within iManage Control Center.
To assign the global Key Management privilege within iManage Control Center:
Create a global role with this Key Management privilege enabled. See Roles.
Assign this role to specific users. See Assigning a role to to a user.
Registering a key
Use this to register (add) a new master key. The master key is the key that is activated on libraries.
A master key must be registered (added) before being activated. Within iManage Control Center, navigate to the Encryption Keys page (Settings > Encryption Keys):
Select Add Encryption Key. The Add Encryption Key dialog box displays.
Figure: Add Encryption Key page
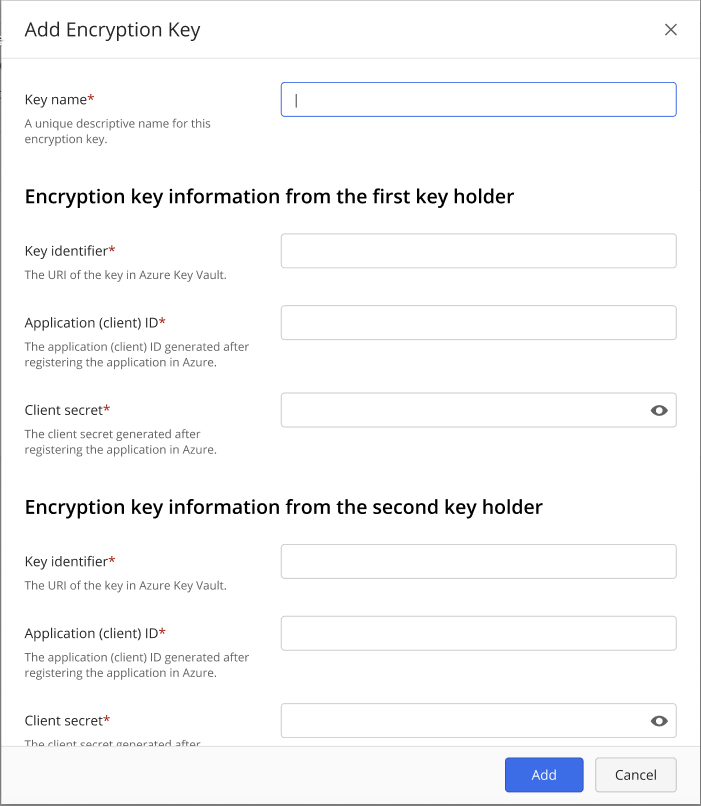
Enter the Key name. This is a descriptive name intended to conveniently identify the key. This name is displayed in the key list. It cannot be the same as another existing key but can be changed later.
The first key holder enters the following:
Key identifier. Also called the Azure Key Version Key Identifier, this is the combination of the URI and key identifier from the process used to create the Azure key vault. Use the value recorded on line 2 of the Azure Information Worksheet for the Azure Key Version Key Identifier. For example: https://azurevault1.vault.azure.net/keys/ajubalaw-2/7668e37b63f6433fa285434f23a58b1b
Application (client) ID. This is a string identifier provided during the application registration in the Azure Active Directory. Use the value recorded on line 3 of the Azure Information Worksheet for the Application ID. For example: https://azurevault1.vault.azure.net/keys/ajubalaw-2/7668e37b63f6433fa285434f23a58b1b
Client secret. This is a client secret provided during the application registration in the Azure Active Directory. Use the value recorded on line 4 of the Azure Information Worksheet for the Client secret. For example: xCGRvvvQmKfqwTw[@a@qovRN_Nn72K46
All of these values must be different than the second key holder's values.
The second key holder enters their information in the same way. All of these values must be different than the first key holders values.
Select Add. This creates the master key. The newly added key will be marked as Ready.
Using the iManage system key
The iManage Work system provides a built-in key called the iManage system key. For some iManage Work environments, encryption is required and this is the default key for the encryption. Customers not wanting to implement and to manage their own keys do not have to do anything to use this key. This key is always available. Customers who are using their own keys and no longer want to manage them, can activate the iManage system key instead.
Activating a key
Use this to activate a master key.
A master key is activated by applying it to libraries. Master keys can be activated on libraries as needed. The previous master key is deactivated. iManage recommends not reusing previously used master keys. The exception is the built-in iManage system key can always be activated even if it had been replaced earlier.
Within iManage Control Center, navigate to the Encryption Keys page (Settings > Encryption Keys):
Right-click a master key (including the iManage System Key), a nd select Activate. The Activation dialog box displays.
Select the library or libraries that you would like this master key to apply to. The libraries the master key can be applied to will be available to be selected in the Activation dialog box.
Select Activate. The Encryption Keys page displays. This newly activated master key will be used in all the encryptions going forward. While a master key is active on a library, it is called a library key. Documents will always be encrypted and decrypted with the library key.
A library key cannot be deselected or deactivated. It becomes deselected or deactivated only when a new master key is activated on that library, in essence replacing the library key.
Editing the key name
Use this to edit a master key name. Editing the key name does not change the status of the master key.
Within iManage Control Center, navigate to the Encryption Keys page (Settings > Encryption Keys):
Right-click the master key name to be edited.
Select Edit. The Edit dialog box displays.
Enter the new master key name. The name cannot be the same as another master key name.
Select Save.
Viewing key details
Use this to view master key details. This provides details about the key and its activated libraries.
Within iManage Control Center, navigate to the Encryption Keys page (Settings > Encryption Keys), and select the master key name to be viewed. The details screen displays.
Terms
The following terms are used during for encryption key process.
|
Term |
Meaning |
|
Activated |
A master key that is currently being used to encrypt documents. |
|
Activation |
The ceremony, or process, that a master key becomes the actively used key for encrypting data. See Activating a key. |
|
Activated date |
The date the master key entry was activated. See Adding a key. |
|
Application (client) ID |
The first of two string identifiers provided during application registration in the Azure Active Directory. The other identifier is the Client secret. Each key holder will have a different Application (client) ID. See Client secret for the second identifier. |
|
Customer-managed encryption key (CMEK) |
The general term for the process in which the customer supplies and manages their own encryption keys. Customers control their entire process, from generating the customer supplied encryption key (the source key), to loading the keys into iManage Work, deciding when to use each key, and when to revoke or replace keys. The iManage Work version implements a dual-party process that requires validation of two independent key stores. |
|
Customer supplied encryption key |
This is the source encryption cipher that will be the basis for the master key used to activate encryption for libraries. The customer creates their own source encryption key and independently copies it to two team members, called key holders. |
|
Global key management privilege |
This is a the global Key Management privilege. With the privilege enabled, users can see the Encryption Key menu item in iManage Control center. CMEK operations using iManage Control Center requires key holders to have global Key Management privilege enabled but not have to be NRTADMINS. NRTADMINs must have the global Key Management privilege enabled. For more information, see Global role setting of Key Management. |
|
iManage |
The customer's designated customer service manager (CSM) or their implementation partner. This an iManage-designated system administrator who must register each of the key holders key store information. |
|
iManage system key |
The built-in key provided by and managed by the iManage Work system. This is a default master. Customers can use this key instead of providing their own. |
|
Key address |
This is a URI of a key holder's Azure key vault that contains the master key. Each key holder will have a different address. |
|
Key health |
The condition, or health, of a key's ability to be accessed. It is one of the following values: Available. The key can be accessed and has the ability to be actively used for encryption/decryption. Unavailable. The key cannot be accessed and its ability to be actively used cannot be assessed. It has not been revoked but only that access to it be being hindered, such as from a network outage. Revoked. The key has been revoked, or temporarily disabled, by the customer. A single unrevoked key is still able to encrypt or decrypt documents. If the revocation is not intended, the cause should be quickly evaluated. Two revoked keys will not be able to encrypt or decrypt documents. Intentionally revoking both keys represents an extreme case, likely due to a catastrophic security event. Keys can be unrevoked at any time by the customer. |
|
Key holder |
A key holder is a customer user who created a separate Azure key vault that contains a copy of the customer supplied encryption key. There will be two key holders, known as key holder 1 and the key holder 2. |
|
Master key name |
The name of the master key entry in iManage Control Center. This is is a descriptive name used to easily identify the master key. The name may be changed later. The name cannot be the same as another master key name. |
|
Key version |
This is a 32-character string identifier provided during the Azure key generation process. Each key holder will have a different key version. |
|
Libraries |
The target library or libraries that the encryption affects. A library itself is not encrypted, only the documents within a library are. |
|
Master key |
The key used to activate on libraries that allows the encryption and decryption of documents. Master keys appear in iManage Control Center Encryption Keys page. It is created by the customer from the two key holders who independently stored a copy of the same customer supplied encryption key in secure Microsoft Azure vaults. Links to those vaults are provided to their iManage Work system administrator. After iManage Work validates the two Azure vaults, the master key is generated. |
|
NRTADMIN |
An iManage Work user with NRTADMIN system administration privileges. This is a user has been added to the NRTADMIN group for the specified library. It is possible a user can be an NRTADMIN for some libraries but not others. As a result, attention must be made to which libraries an NRTADMIN is attempting to active an encryption key for. |
