NOTE: To perform operations on this page, the user must be a member of the NRTADMIN group. For more information about the specific operations allowed, refer to Understanding tiers.
This page contains information to help you configure and manage Security Assertion Markup Language (SAML) single sign-on (SSO) authentication in your iManage environment, and update your configuration when Identity Provider (IdP) certificates are nearing expiration and need to be refreshed.
Configuring SAML SSO for your iManage environment offloads user authentication to your IdP and provides the following benefits:
Simplifies the user authentication experience.
Reduces the cost of user account administration, such as managing or resetting passwords for your users.
iManage uses Service Provider-initiated SAML SSO, where iManage is the service provider. When a user attempts to sign in, an SAML Authentication Request is sent to the IdP to authenticate the user.
Prior to the Q3 2021 Cloud Service Update / iManage Work 10.4.0 release, iManage used Identity Provider-initiated SAML SSO. By migrating to SP-initiated SAML SSO, customers can manage their SAML SSO configuration entirely within iManage Control Center and their Identity Provider. Migrating from IdP-initated to SP-intitiated SAML SSO has no impact to the sign in process for your users.
Who should use this?
New customers who are adopting iManage Work and want to implement SAML SSO authentication for their users
Existing iManage Work customers who aren't currently using SAML SSO and want to transition to SAML SSO authentication for their users.
Existing iManage Work at imanage.work customers who are currently using SAML SSO authentication as configured and managed by iManage, and want to manage their SAML SSO authentication directly using iManage Control Center.
On this page:
Before you begin
Before you configure SAML SSO in your iManage environment:
Confirm that at least one administrative user account with the OS Type of Virtual is created within all iManage Work libraries. Use this account to configure SAML SSO in the following sections on this page.
When set to Virtual, these accounts use explicit sign-in to authenticate to iManage Work. That is, they use the user email and password as defined in iManage Control Center and don't authenticate using SAML SSO.
Refer to the steps below to confirm the OS type of an iManage user. Confirm that these administrative users can sign in to iManage Work.
CAUTION: If you don't configure at least one virtual user account in all libraries, and your SAML SSO authentication is improperly configured, or your IdP certificate expires, all users will be blocked from signing in to iManage.
Confirm these administrative users can sign in to Work 10 Web using the explicit sign-in URL:
https://<domain>/login/imanagework.html
Confirm that all other iManage user accounts used for authenticating iManage services (such as the account used for iManage Directory Synchronization Service, iManage Refile Service, or Workspace Generator) or third-party integrations are configured with the OS Type of Virtual.
We recommend that all other iManage user accounts be defined with the OS Type of Active Directory. This enforces SAML SSO authentication for these users, and prevents them from signing in using explicit sign-in. Any users imported using the iManage Directory Synchronization Service are automatically set to Active Directory.
To confirm the OS Type of a user:
In iManage Control Center, browse to Access > Users.
Select any user account.
In the Platform Details section of the user's account, view the OS Type field.
To change the OS Type for an individual user so that they are configured to authenticate using SSO:
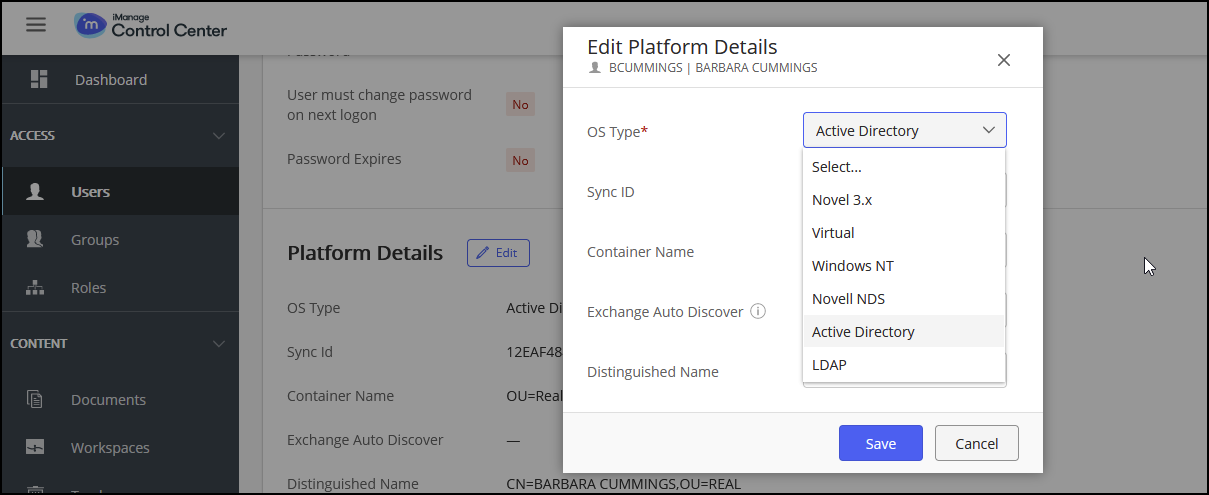
In the Platform Details section of the user's account, select Edit. The Edit Platform Details dialog opens.
Select Active Directory, and then select Save.
Figure: Edit Platform DetailsIf you require assistance updating a large number of users, contact support@imanage.com.
Steps to configure SAML SSO
Get the XML file from your Identity Provider
After you complete the steps in Configure your Identity Provider SSO, your IdP will provide you with an XML file. This file contains information about your federation service that's used to create trusts and identify token-signing certificates. Importing this file to iManage Control Center, as described in Enable SAML SSO, assigns values to the following SAML SSO configuration fields:
Identity provider SSO URL: The URL of the SAML SSO Identity Provider.
Logout URL: The URL used to redirect a user's browser window to a sign-out endpoint to end their authentication session and sign them out.
Certification expiration date: The expiration date of your Identity Provider signing certificate.
Configure your Identity Provider SSO
To configure your Identity Provider to provide SAML SSO authentication for your iManage users, see the following instructions for your IdP:
For all other Identity Providers, refer to General IdP configuration.
After you've configured your IdP and downloaded the Federation XML metadata file from your IdP, continue to Enable SAML SSO.
Enable SAML SSO
The following steps describe how to import the Federation XML metadata file and enable SAML SSO for your iManage users in iManage Control Center.
TIP: To avoid disruption due to a misconfiguration, we recommend that you perform these steps during a maintenance window or when very few people are using iManage Work.
Sign in to iManage Work using the administrative Virtual account, as described in Before you begin, using the explicit login page:
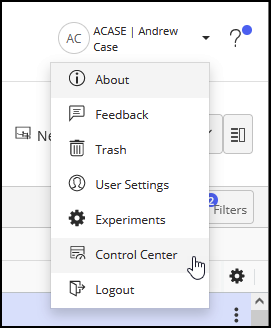
https://<domain>/login/imanagework.htmlIn the iManage Work user profile menu, select Control Center to open iManage Control Center.
Figure: Accessing iManage Control CenterBrowse to Network & Security > Single Sign-On (SSO).
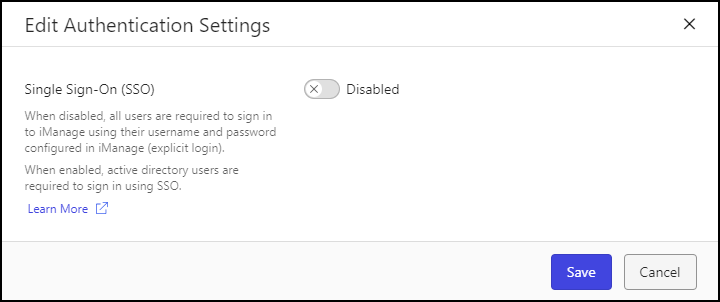
In the Authentication section, select Edit. The following dialog opens:
Figure: Edit Authentication SettingsSelect Enabled.
Select Next. The Setup SAML Single Sign-On (SSO) dialog opens, and displays the information for your iManage environment. Confirm that the service provider settings are correct.
NOTE: If you haven't already performed the steps in Configure your Identity Provider SSO, read and perform those steps before continuing.
Select Next. The Setup SAML Single Sign-On (SSO) dialog displays the Configure SAML SSO section.
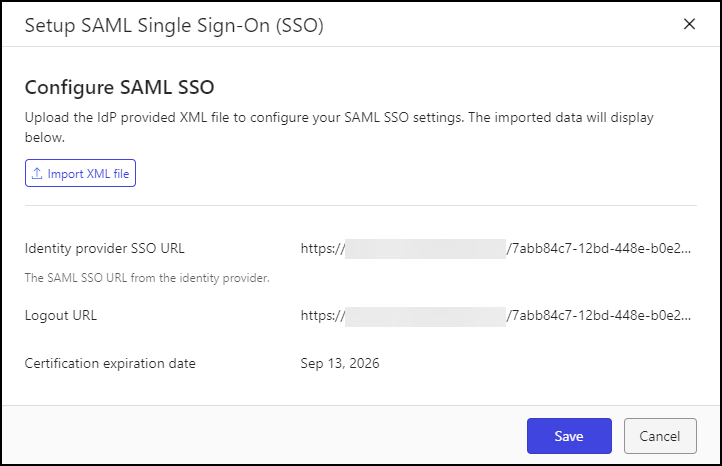
In the Configure SAML SSO section, select Import XML file.
When prompted, locate the metadata XML file that you downloaded from your IdP in Configure your Identify Provider SSO, and then select Open.
The file is imported into iManage Control Center and the values for Identity provider SSO URL, Logout URL, and Certification expiration date are displayed based on the information in the metadata XML file.
Figure: Setup SAML Single Sign-On (SSO)Before continuing, confirm that the Certification expiration date displayed in iManage Control Center matches what you configured in your IdP and that it isn't expired. Having an expired or improperly loaded certificate will prevent iManage users from signing in successfully using SSO.
Select Save.
SAML SSO is now configured in your iManage Cloud environment. Continue to Validate that users can sign in to iManage Work.
Validate that users can sign in to iManage Work
After SAML SSO is configured and enabled in iManage Control Center, users can begin signing in to iManage Work. Depending on the Identity Provider you are using, this may take several minutes to become active.
If users aren't able to sign in successfully, refer to Troubleshooting.
Update your IdP certificate
After configuring SAML SSO, you must monitor the expiration of your IdP certificate. When the certificate is nearing expiration, you must generate a new Federation metadata XML file from your IdP and import it into iManage Control Center. This file includes the new certificate.
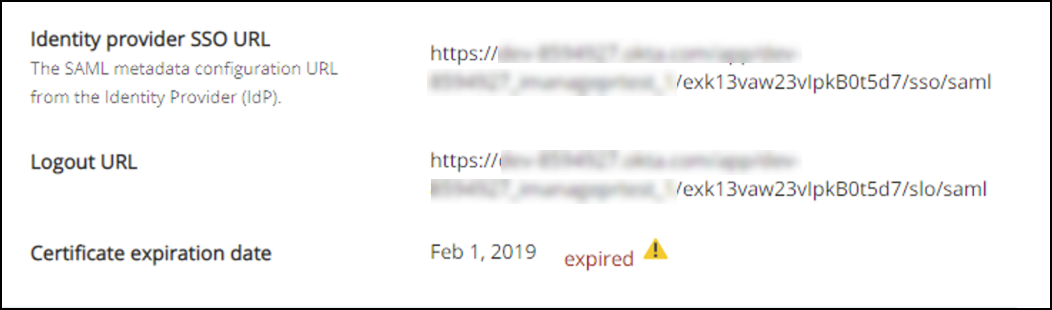
To view the expiration date of your current signing certificate in iManage Control Center, browse to Network & Security > Single Sign-On (SSO) and view the Certification expiration date field.
iManage Control Center displays a message if the certificate is expiring within the next 45 days, or has already expired.
IMPORTANT: It's your responsibility to follow these steps whenever the certificate has changed within your IdP, or if it is set to expire soon. If your SAML Signing Certificate changes or expires without importing it into iManage Control Center, users will be unable to sign in to iManage Work. If this occurs, only users with OS Type set to Virtual will be able to sign in using explicit sign-in.
To update your IdP signing certificate:
In your IdP, download the new Federation metadata XML file for your SSO configuration. If needed, upload the updated signing certificate into your IdP SSO configuration before downloading the Federation metadata XML file.
In iManage Control Center, browse to Network & Security > Single Sign-On (SSO).
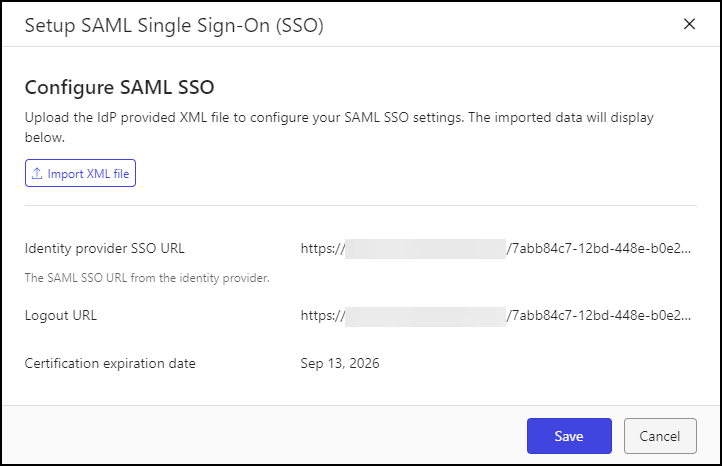
In the Configure SAML SSO section, select Import XML file. The following dialog opens.
Figure: Setup SAML Single Sign-On (SSO)Select Import XML file.
When prompted, locate the metadata XML file that you downloaded from your IdP that contains your new certificate, then select Open.
The file is imported into iManage Control Center, and details such as Certification expiration date are displayed. Confirm that the Certification expiration date field displays the new date.
Select Save.
Troubleshooting
After enabling SAML SSO, if users can’t sign in to iManage Work using SSO or if they receive a “SAML Login Error: invalid_response” error message, perform the following steps to resolve this issue:
Verify your SSO configuration in your IdP. Review the detailed instructions and troubleshooting information on the following IdP configuration pages:
Confirm that the certificate expiration date shown in iManage Control Center isn't expired.
Confirm that your Identity Provider service is available. If it is offline, contact your Identity Provider directly.
If you're unable to determine the cause of the issue, contact iManage Support (cloudsupport@imanage.com or support@imanage.com).
FAQ
Q: How will I know when my certificate is about to expire?
A: Your certificate's expiration date is shown in the Certification expiration date field on the Single Sign-On (SSO) page in iManage Control Center. iManage Control Center also includes a warning message when the certificate expiration date is within 45 days, or if it is expired. For more information, refer to Update your IdP certificate.
Q: How does SAML SSO affect iManage users who are defined with OS Type = virtual in iManage Control Center?
A: Users configured as virtual users must use their username and password defined in iManage Work. They can sign in to iManage Work using the explicit sign-in URL: https://<domain>/login/imanagework.html
If you have service accounts which are set to OS Type = Active Directory, set these to OS Type = Virtual before enabling SAML SSO.
Q: I just enabled SAML SSO and now my administrative users aren't able to sign in using their username and password as defined in iManage Control Center.
A: Confirm that these users are set with OS Type of Virtual in their user profile in iManage Control Center. For more information, refer to Before you begin.
Q: Our company has a Utility Service URL available in our iManage Work in the Cloud environment. Should I configure SAML SSO for this Utility Service URL?
A: A Utility Service URL is generally used to offload third-party tools or services that need access to your iManage Work environment. As a best practice, don't configure SAML SSO for your Utility Service URL(s), because this would result in sign-in issues for your users. If you need to sign in to this system, you must access this with the explicit sign-in URL: https://<domain>/login/imanagework.html