App policy configurations
The following settings must be defined in the iOS Managed App Configuration in Intune.
IMPORTANT:
The following settings must be configured as shown for the iManage Work Mobility for Intune app to be deployed:
- version = 2
- allow_safari_for_login = false
The following settings must be configured for the iManage Work Mobility for iOS app to be deployed:
- server0_uuid
- server0_name
- server0_auth
- server0_url
enable_downloading
enable_printing
enable_airdrop
enable_native_email
open_in_send
open_in_receive
enable_privacy_curtain
enable_touch_id_for_passcode
number_of_passcode_retries_min_3_max_20_default_10
passcode_grace_period_seconds_min_10_max_999999999_default_60
show_demo_connection
NOTE:
The following table lists the key-value pairs settings that must be specified:
Table: Key-value Pairs
Identifier | Type | Default | Description |
|---|---|---|---|
version | Integer | 2 | Specifies the format version for configuration and is required. It must be set to 2. |
open_in_receive | Boolean | true | Use this policy to restrict users from receiving document(s) in iManage Work Mobility from other applications. true: Users can import documents to iManage Work Mobility for Intune from other applications. false: Restricts the users from importing documents to the iManage Work Mobility for Intune from other applications. NOTE:
|
open_in_send | Boolean | true | Use this policy to restrict users from sending document(s) in iManage Work Mobility for Intune to other applications. true: Lets users send documents from iManage Work Mobility for Intune to other applications through Open In feature of iOS. false: Documents can't be sent from iManage Work Mobility for Intune to other applications. NOTE:
|
enable_native_ | Boolean | true | Use this policy to restrict users from sending document(s) as email attachment from iManage Work Mobility for Intune through native email (Mail app) application. true: Lets users send the iManage Work document(s) as email attachments using the iOS Mail app. false: Prevents users from sending iManage Work document(s) as email attachments. NOTE:
|
enable_airdrop | Boolean | true | Use this policy to restrict users from sharing documents in iManage Work Mobility for Intune using AirDrop. Apple's AirDrop feature enables the transfer of files between supported Macs and iOS devices without using mail or a mass storage device. true: Lets the user share the downloaded documents through AirDrop. false: Disables sharing the documents through AirDrop. NOTE:
|
enable_printing | Boolean | true | IMPORTANT: If your MDM policy configuration restricts emailing documents out of iManage Work Mobility for Intune, users can use Print Preview of a PDF to get around this, as it can be distributed through iOS Mail app. Apple bug report # - 45524779 . Use this policy to restrict users from printing documents from iManage Work Mobility for Intune. true: Lets users print downloaded documents through iOS AirPrint. false: Disables the printing of documents. NOTE:
|
enable_ | Boolean | true | Use this policy to restrict users from downloading documents to their mobile devices from iManage Work Mobility. true: Documents may be downloaded to the device. false: Prevents bulk download of documents to the device |
enable_privacy_ | Boolean | true | Privacy Curtain is a security feature that obscures the contents of iManage Work Mobility for Intune when the application isn't active. This setting isn't applicable to iManage Work Mobility for Intune. To set this in Intune, access Client Apps > App Protection Policies > Properties> Access Requirements. |
enable_touch_id_ | Boolean | true | Enables users to sign into iManage Work Mobility for Intune through Touch ID or Face ID on their mobile device. This setting isn't applicable for iManage Work Mobility for Intune. To set this in Intune, access Client Apps > App Protection Policies > Properties> Access Requirements. |
show_demo_ | Boolean | true | Server connection that connects to a public iManage demo server, which can be used to test the iManage Work Mobility for Intune application before it is deployed in your environment. true: The Demo connection is displayed at the bottom of the servers list on the sign in screen. false: The Demo connection isn't displayed. NOTE:
|
number_of_ | Integer | 10 | The number of times the application passcode can be entered before all locally stored data is erased from the device (no data is impacted on the server). This setting isn't applicable to iManage Work Mobility for Intune. To set this in Intune, access Client Apps > App Protection Policies > Properties > Access Requirements. |
passcode_grace_ | Integer | 10 | When switching away from the application, there's a time delay before the App Lock is enforced, requiring the user to enter the application passcode (or if configured, Touch ID). The minimum is 10 seconds; the maximum is 999999999 seconds (effectively only requiring the user to enter the application passcode or use Touch ID when the application starts or restarts). This setting is not applicable for iManage Work Mobility for Intune. To set this in Intune, access Client Apps > App Protection Policies > Properties> Access Requirements. |
prevent_copy_to_clipboard | Boolean | false | Use this policy to restrict users from copying content in iManage Work Mobility for Intune, and pasting it into clipboard or pasteboard. This policy configuration secures iManage Work data. false: This setting is the default, and it allows users to copy text from an iManage document to other applications. true: The clipboard or pasteboard in iManage Work Mobility for Intune is cleared when a user copies text from any document. This effectively stops copying any data from iManage Work Mobility for Intune as the user can't paste any text into other application(s). IMPORTANT: This feature may be restricted or disabled due to MDM policies. |
view_mode | Boolean | false | Use this policy to offer users a View-Only experience in iManage Work Mobility for BlackBerry Dynamics. Disabled (default): This allows the user to:
Enabled: This setting prevents the user from performing the following activities:
When enabled, this setting supercedes the open_in_receive and enable_app_extensions settings. Even if those are enabled, the app will not honor them when this policy setting (view_mode) is enabled. NOTE: After this policy is enabled, when users edit a document and try saving it back to the iManage Work Mobility app, the following error message appears: |
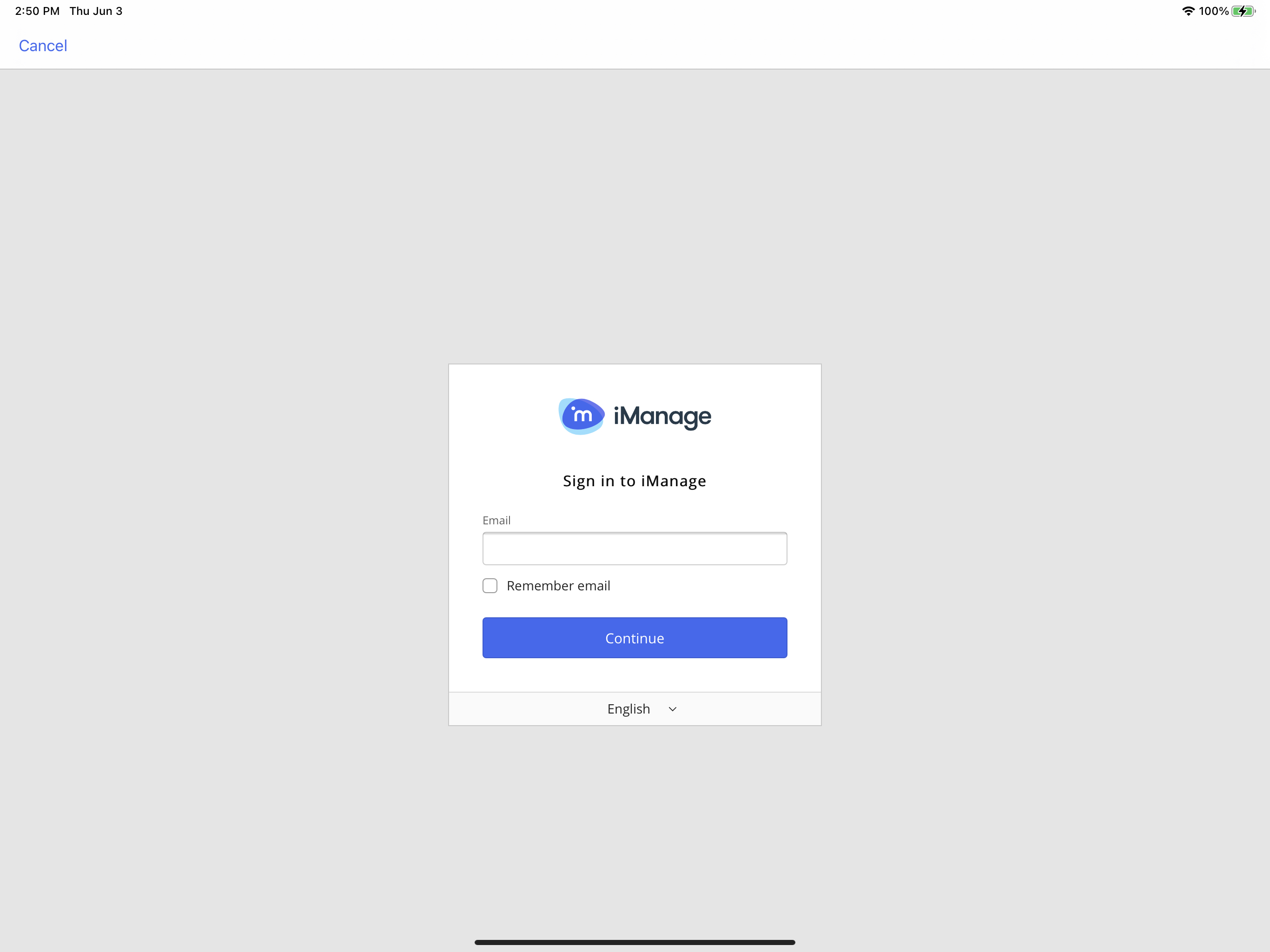
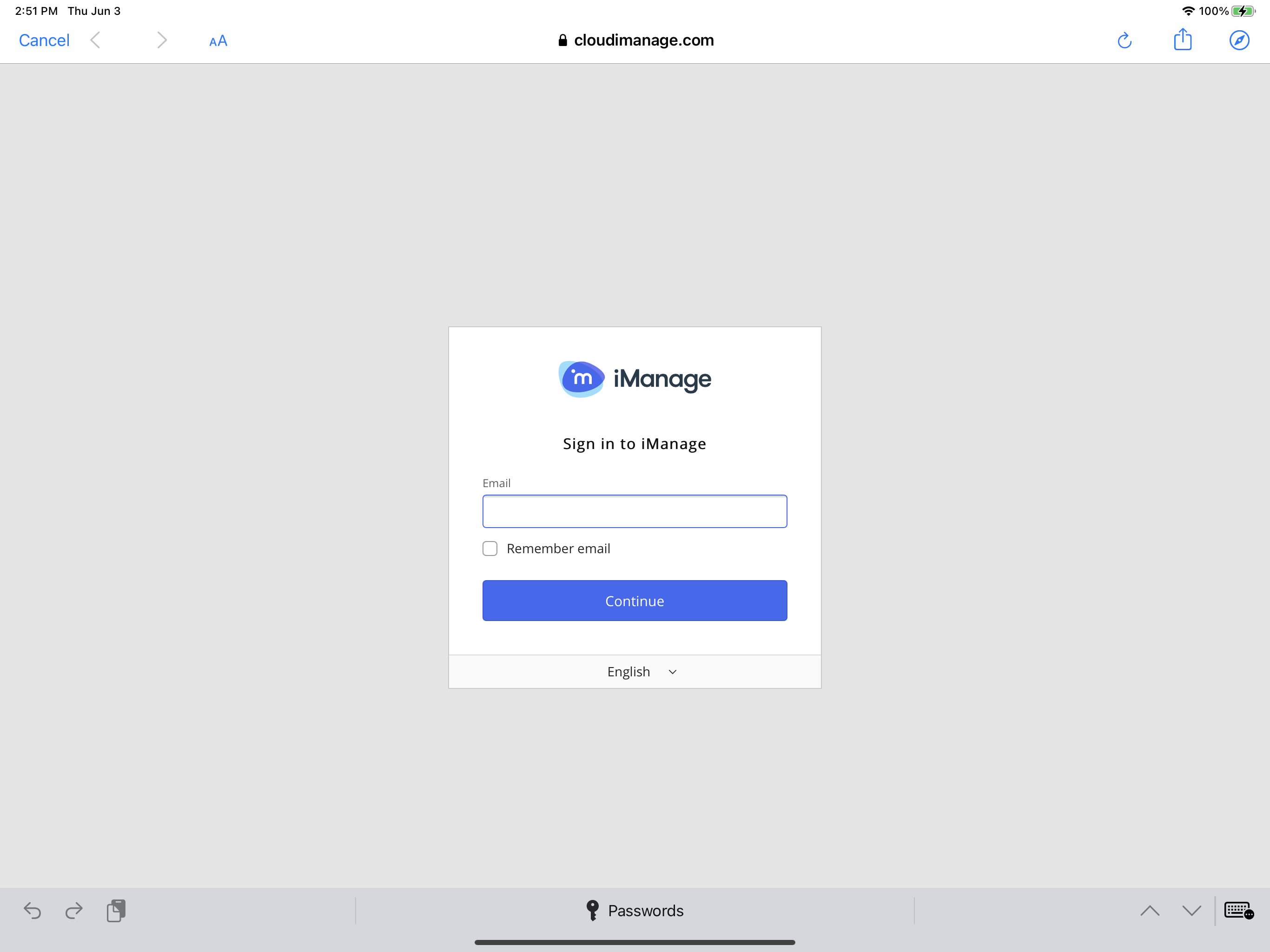
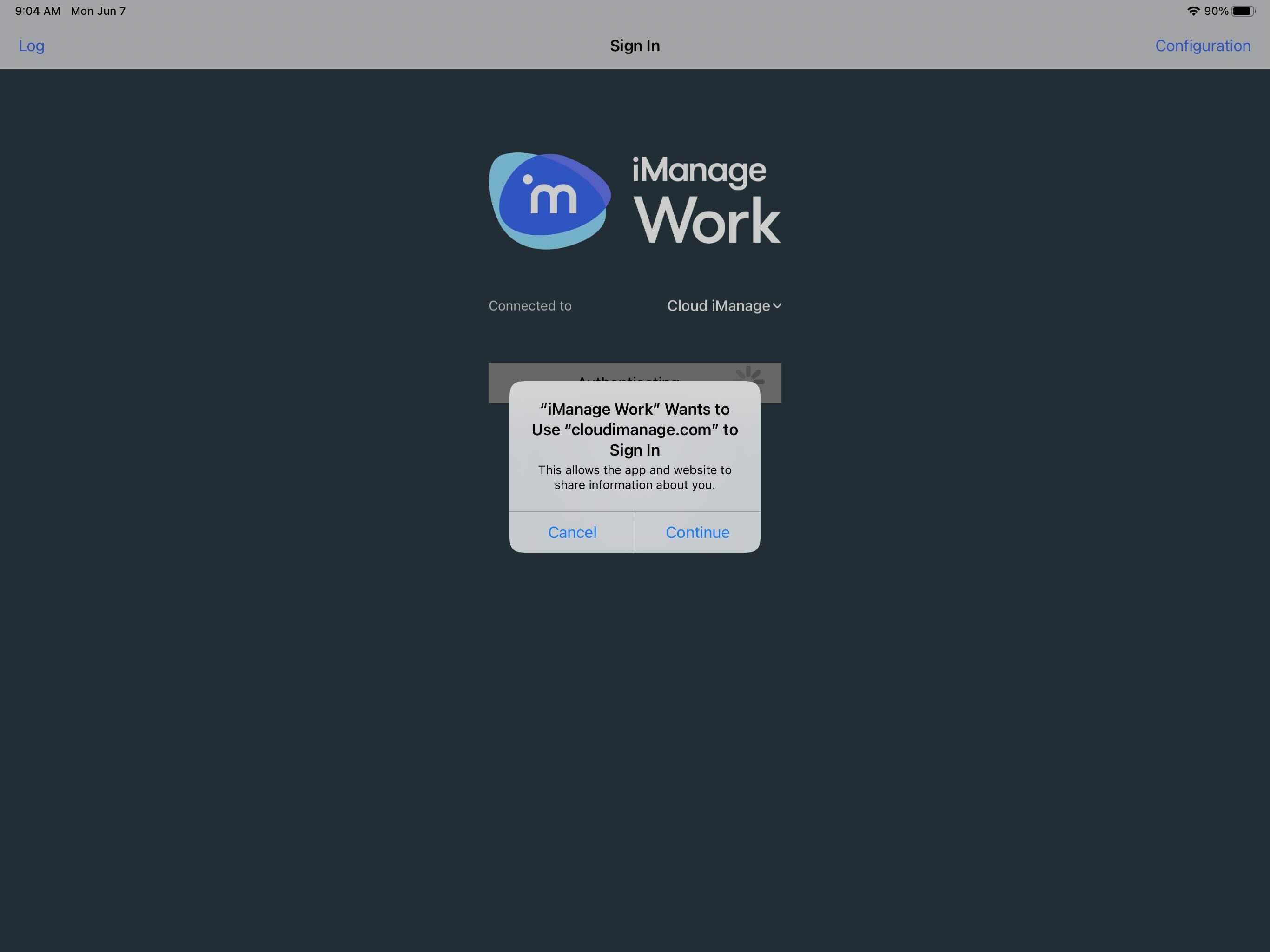
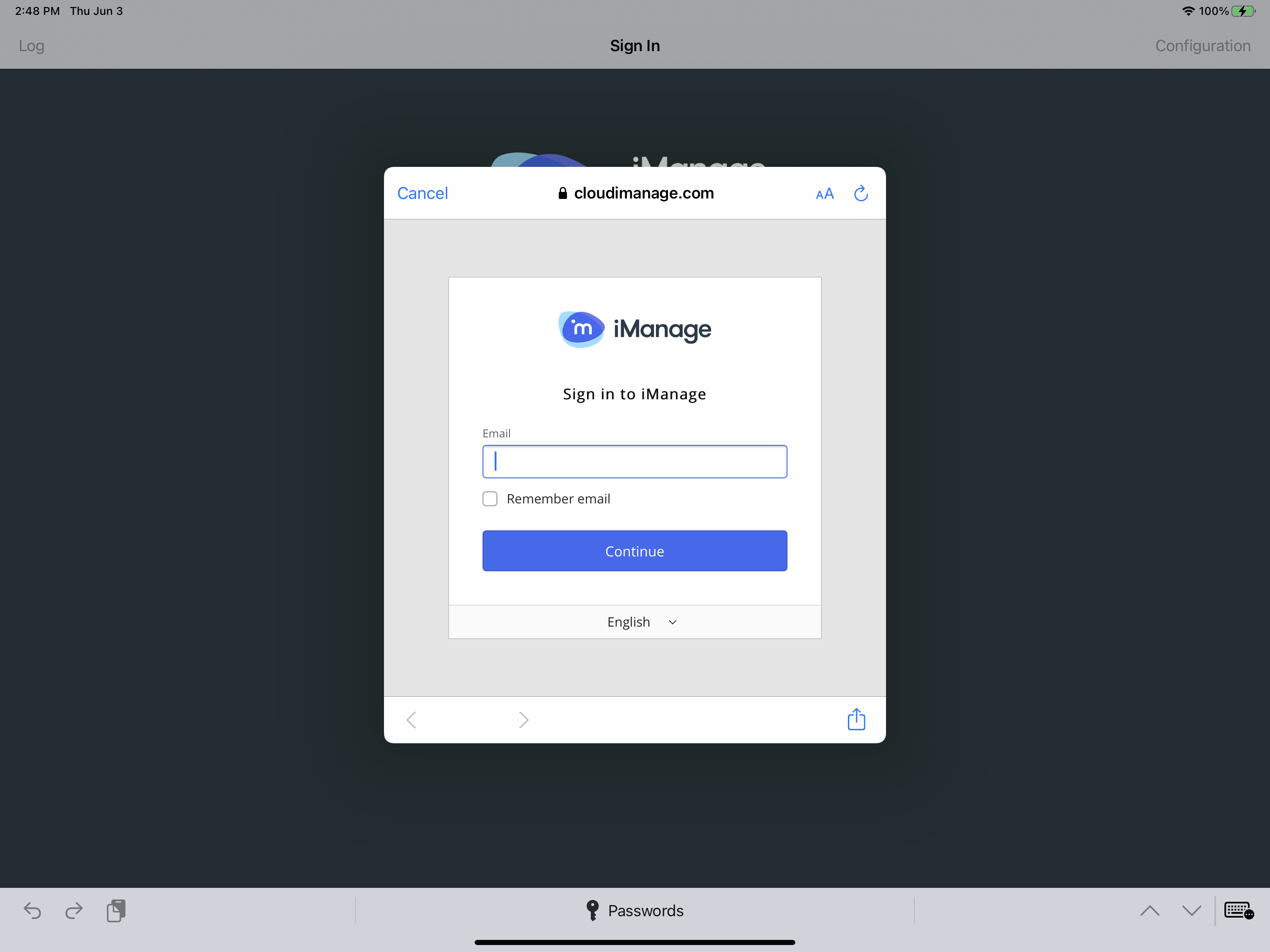
web_authentication_mode | Integer | For existing deployments, no default (not set). For new deployments, the default is 2 (ASWebAuthenticationSession). | Use this policy setting to control which web-based authentication controller (embedded browser) is used when users are prompted to sign in to iManage Work. 0 – WKWebView: Enables the legacy embedded web-based authentication controller, WKWebView. Figure: Sign in screen for WKWebView 1 – SFSafariViewController: Enables the Safari-based web-based authentication controller, SFSafariViewController. Figure: Sign in screen for SFSafariViewController The primary difference to the user is the addition of the browser buttons at the top of the screen. 2 – ASWebAuthenticationSession: This is recommended by iManage. Enables Apple's latest ASWebAuthentication embedded web view controller for web-based authentication. NOTE: With option 2, the first time a user attempts to sign in to iManage Work, they're presented with a prompt. Users must tap Continue to proceed to the iManage Work sign in screen, as shown in the second figure below. Figure: User confirmation prompt during initial sign in - ASWebAuthenticationSession 3 – Default browser: Rather than using an embedded web view or web view controller, the app switches to the iOS default browser, and when authentication is complete, the browser switches back to the Work 10 app. By default, the default browser is Safari, but the user can change this to any browser such as Edge or Chrome. 4 – Microsoft Edge browser (if installed): Similar to 3 above, but instead of loading the default browser, a specific URL for Microsoft Edge is used. If the user has specified a different default browser and authentication needs to be on Edge, use this setting. If Edge isn't installed, no sign-in screen is displayed and the user isn't able to sign in. 5 – Google Chrome browser (if installed). Similar to 3 above, but instead of loading the default browser, a specific URL for Google Chrome is used. If the user has specified a different default browser and authentication needs to be on Chrome, use this setting. If Chrome isn't installed, no sign-in screen is displayed and the user isn't able to sign in. 6 – AirWatch/VMware Workspace One browser (if installed): Similar to 3 above, but instead of loading the default browser, a specific URL for Workspace One is used. If the user has specified a different default browser and authentication needs to be on Workspace One, use this setting. When set, this web_authentication_mode policy setting replaces the allow_safari_for_login policy setting. For customers who have already deployed iManage Work Mobility:
For customers deploying iManage Work 10.20.2 or later for the first time:
NOTES:
|
allow_safari_for_ | Boolean | true | IMPORTANT: IMPORTANT: For Intune deployments using web-based authentication (serverx_auth=1,2.3), you must set allow_safari_for_login to false. Intune does not support allow_safari_for_login. Use this policy to restrict users from signing in to the application using Safari in iManage Work Mobility for Intune. NOTE: If web_authentication_mode is set to any value, this allow_safari_for_login setting is ignored. true: This setting is the default. When users select Sign In on the Work Mobility application, they're directed to a new Safari window to sign in using their company credentials. NOTE: When set to true, Safari allows users to save their credentials in the secure iOS Keychain. false - When users select Sign In on the Work Mobility application, they're directed to an embedded web view window to sign in using their company credentials. |
enable_analytics | Boolean | true | This policy controls whether a user will be prompted to opt in or out of sending analytics to iManage. It doesn't explicitly set up analytics on the app. This option is enabled by default. NOTES:
|
login_user_account_auth0_only | String | - | Allows you to optionally enter a UserID in the sign-in dialog. This applies only when Server Authentication is set to 0 - Standard/Explicit. |
IntuneMAMUPN | String | - | iManage Work Mobility for Intune is supported on managed devices and can be configured as a Managed App within the Device Enrollment Type settings in Intune. For more information, refer to: https://docs.microsoft.com/en-us/mem/intune/apps/app-configuration-policies-use-ios. If using a managed device configuration setting instead of a managed app configuration, include this application policy setting and set it to: {{UserPrincipalName}} There must be no spaces after {{ or before }}. |
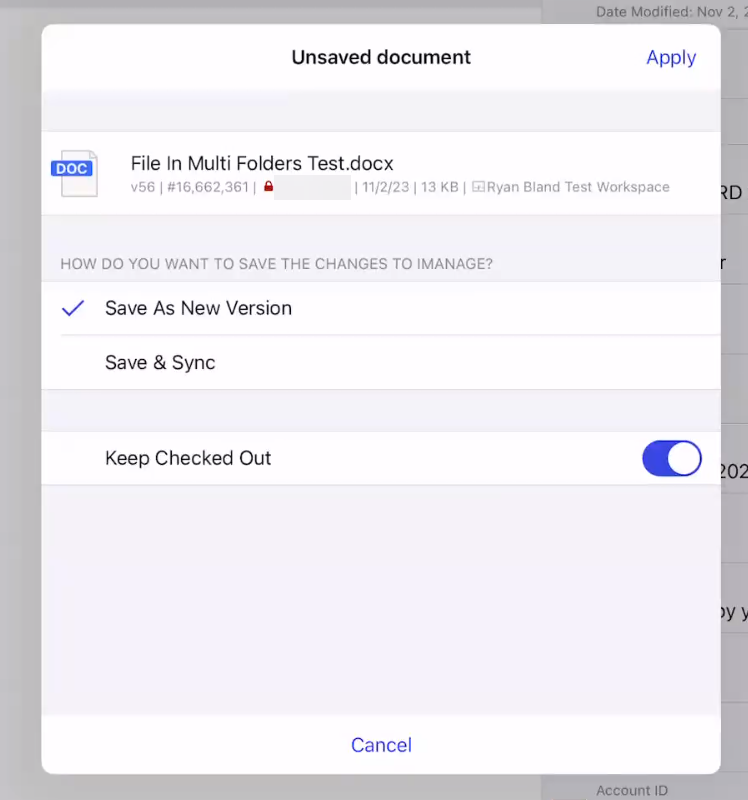
force_user_interaction_on_edit_in_place | Boolean | false | Use this policy to control how the app responds when a user saves edits back to iManage Work. This setting is available in iManage Work 10 Mobility version 10.23.4 and later. false: The default setting. After editing a document opened from iManage Work, navigating back to the iManage Work Mobility app automatically saves the user's changes as a new version of the document. Additional edits to the open document are saved to the same version. When finished with their changes, the user must manually check in the file in iManage Work. true: After editing a document in iManage Work, navigating back to the iManage Work Mobility app prompts the user with the following dialog. This gives the user control over how they want to save their edits.
|
SERVER CONFIGURATION
Any number of servers may be included. These are displayed in numerical order based on the integer in the identifier, starting with 0. For example, server2_uuid is the third server.
NOTE:
You must define the following settings for least one entry (server0) to enable the users to connect.
Identifier | Type | Default | Description |
|---|---|---|---|
server0_uuid | String | - | A universally unique identifier to uniquely identify this entry. These can be generated by visiting https://www.uuidgenerator.net/version4. Example: b985dc4b-3232-4719-9d1d-cf0162badc30 NOTE: After a UUID is assigned to a server, the mapping between the UUID and server can't be altered as this can cause connectivity issues for the clients. IMPORTANT: The UUID can't be blank or duplicated. If any of the servers have a duplicate or blank UUID, that .immconfig file is rejected and a previously passed file is implemented. |
server0_name | String | - | The name that'll be displayed in the app in the list of available iManage Work connections. |
server0_auth | Integer | - | The authentication type for the server. The valid values are: 0 - Standard: Supports both Work credentials and domain/username and password for explicit network authentication. 1 - ADFS (on-premises ADFS Server): Displays an embedded web view where the user must follow whatever authentication procedures the company has defined for the ADFS implementation. 2 - Common login: Provides a single sign-on for iManage Work 10 client applications. The login UI maintains information about the currently signed-in user in its session cookie. 3 - Use Oauth2 Refresh Token and Access Tokens: For more information, refer to Enable access request tokens. This option minimizes the number of times a user is prompted to sign in. Username, password, and access tokens and refresh tokens are stored in the iOS Keychain. |
server0_url | Text | - | The iManage Work URL for users to access iManage Work via this app.
NOTE: Adding HTTPS or ports such as :8000 to this value is ignored. HTTPS and port 443 are always used. SSL/TLS is always used, in accordance with the most secure settings of iOS security. |
For more information on configuration files deployment, refer to Deploying Configuration Files.
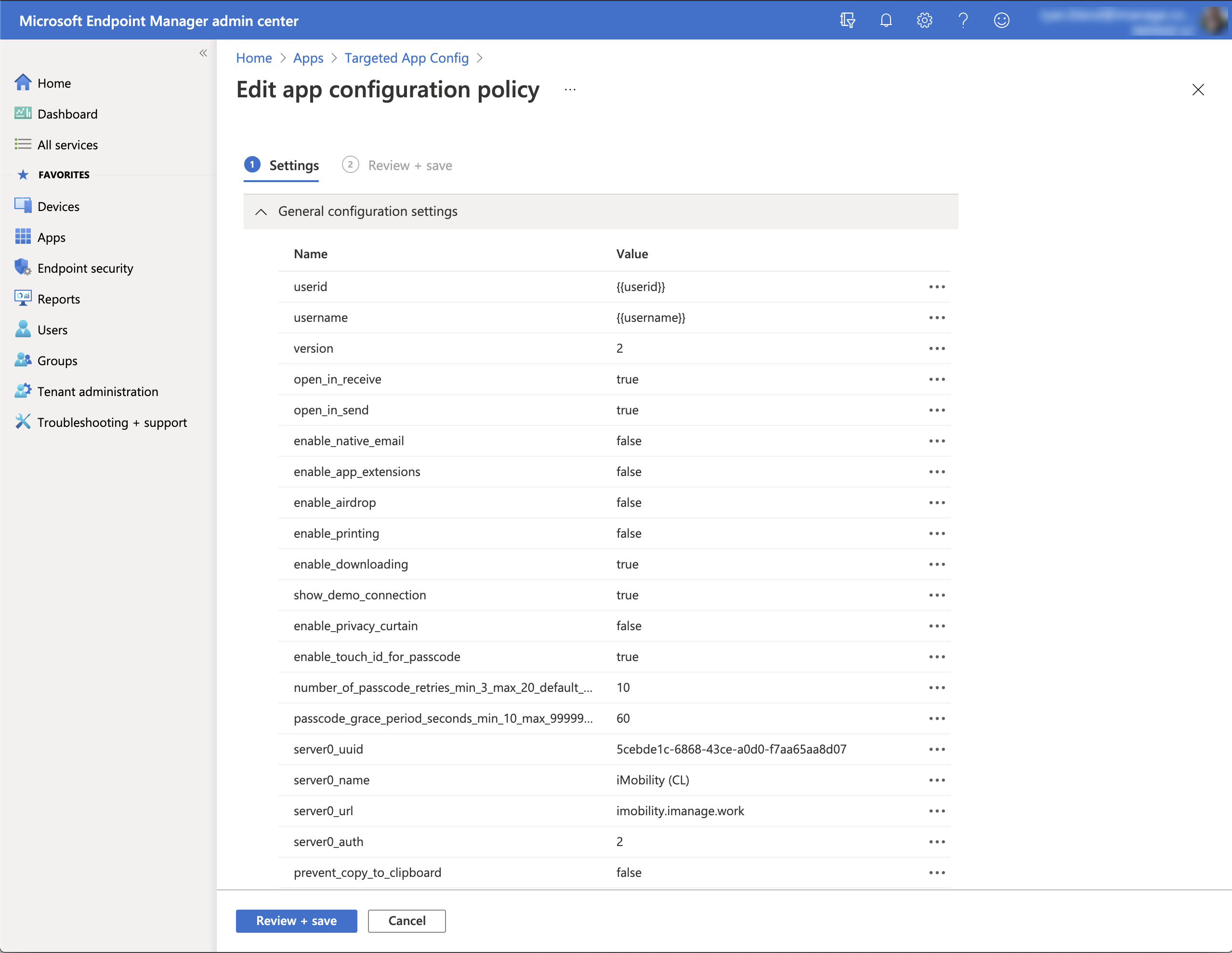
The following figure shows an example of the configured settings in Intune:
Figure: Target App Config - example key-value pairs