In this section, you can find out how to access and get started with iManage Security Policy Manager. Key interface items and terminologies are also provided.
Accessing iManage Security Policy Manager
Before you access the iManage Security Policy Manager application, the iManage Security Policy Manager Server service must be running.
Signing in to the iManage Security Policy Manager application depends on the security model configured by your organization. iManage Security Policy Manager supports SAML-based authentication. For information about SAML authentication, refer to the SAML Authentication section in iManage Security Policy Manager Installation Guide.
Shared authentication with cloudimanage.com
NOTE: This option is only available to iManage SPM in the Cloud customers who are importing user and group definitions from iManage Work at cloudimanage.com.
You can navigate to iManage SPM simply by modifying your cloudimanage.com URL to cloudimanage.com/spm/web.
This means that you no longer need to sign in separately for iManage Work and/or iManage SPM. Custom subdomains are also supported. For example: yourcompany.cloudimanage.com/spm/web.
When you navigate to this type of URL, ending in /spm/web, iManage SPM opens with an amalgamated user and administration console—showing functionality identical to the separate consoles, in accordance with your roles in iManage SPM. This single console contains all of the left navigation bar items of the user console and the administration console, in accordance with the user's iManage SPM roles. For example, a user with only the User role will see only the user console functionality, as before.
Previous SPM sign-in URLs (for example as described in the subsection below) continue to work if you wish to use them, as does SAML authentication if you had been using that.
Form-based authentication
Alternatively, form-based authentication is also allowed in iManage Security Policy Manager. You can set up form-based authentication at the organizational level where every user accesses the application through their user credentials configured in iManage Security Policy Manager, or the user and group administrator can enable access on a user-to-user basis. For more information about enabling form-based sign-in, refer to Enabling Form Login.
If form-based sign-in is enabled for you, there are two options for signing in, depending on whether your iManage Security Policy Manager server is located on premises or in the Cloud.
Form-based sign-in to SPM on-premises
Enter URL of the form http(s)://<host:port>/admin/login in your web browser. The iManage Security Policy Manager sign-in page appears.
NOTE:
The default port is
8080. The port number is the number iManage Security Policy Manager Server service is configured to run under.Depending on how iManage Security Policy Manager Server service is configured, the transport protocol can be either http or https.
In Username and Password, enter your user name and password, respectively.
NOTE:
You may display or hide the password by selecting the icon.
Select Sign In. You are now signed in to the application. The iManage Security Policy Manager Home page appears.
Form-based sign-in to SPM in the Cloud
In your web browser, enter the admin sign-in URL that you have been provided with—for example: https://<OrganizationID>-spm.imanage.work/admin, or https://<OrganizationID>.spm-cloudimanage.com/admin, where <OrganizationID> is the customer ID or vanity URL for your organization. The iManage Security Policy Manager sign in page appears.
In the Username and Password fields, enter your user name and password, respectively.
NOTE:
You may display or hide the password by selecting the icon.
Select Sign In.
You have now signed in to the application. The iManage Security Policy Manager Home page appears.
Resetting the Password
If you signed in using Enabling Form Login, you have the option to change your login password.
Select <User name>, in the upper right corner of the page.
Select Reset Password.
The Reset password page appears. The password requirements are presented on the page to guide you while setting a new password.In the Existing Password field, enter your current password.
In the New Password field, enter a new password conforming to the password requirements.
In the Confirm your New Password field, re-enter the new password you set.
Select Submit.
The new password is now set. Enter the new password when you sign in again.
Signing out
You can sign out of iManage Security Policy Manager.
Select <User name> on the top banner.
Select Sign Out. You are signed out of the application.
Viewing the version of SPM
You can view the version numbers of iManage Security Policy Manager Server and Client.
Select <User name> on the top banner.
Select About. The About dialog appears, showing the SPM version information.
TIP:
If you are using iManage SPM in the Cloud, you can find more information about your server and client versions, and equivalent server version, by referring to How can I determine my Security Policy Manager version? section of the latest Cloud Service Update on iManage Help Center.
Bookmarks
If you are signed in to the application, you can access a specific page in the console by entering the exact URL of the page. However, if you are not signed in and try to access a page through a URL provided to you, you are directed to the sign-in page first, and after you enter your credentials, the application redirects you to the specific page you were trying to access.
NOTE:
If the URL is invalid, then a "404 – page not found" error is displayed.
Understanding the interface
Overview of the SPM administration console interface
Upon successful sign-in to the iManage Security Manager application, the Home Page of the interface displays.
All main sections of the interface can be accessed from the navigation bar on the left. A list and overview of the sections and components available is provided below.
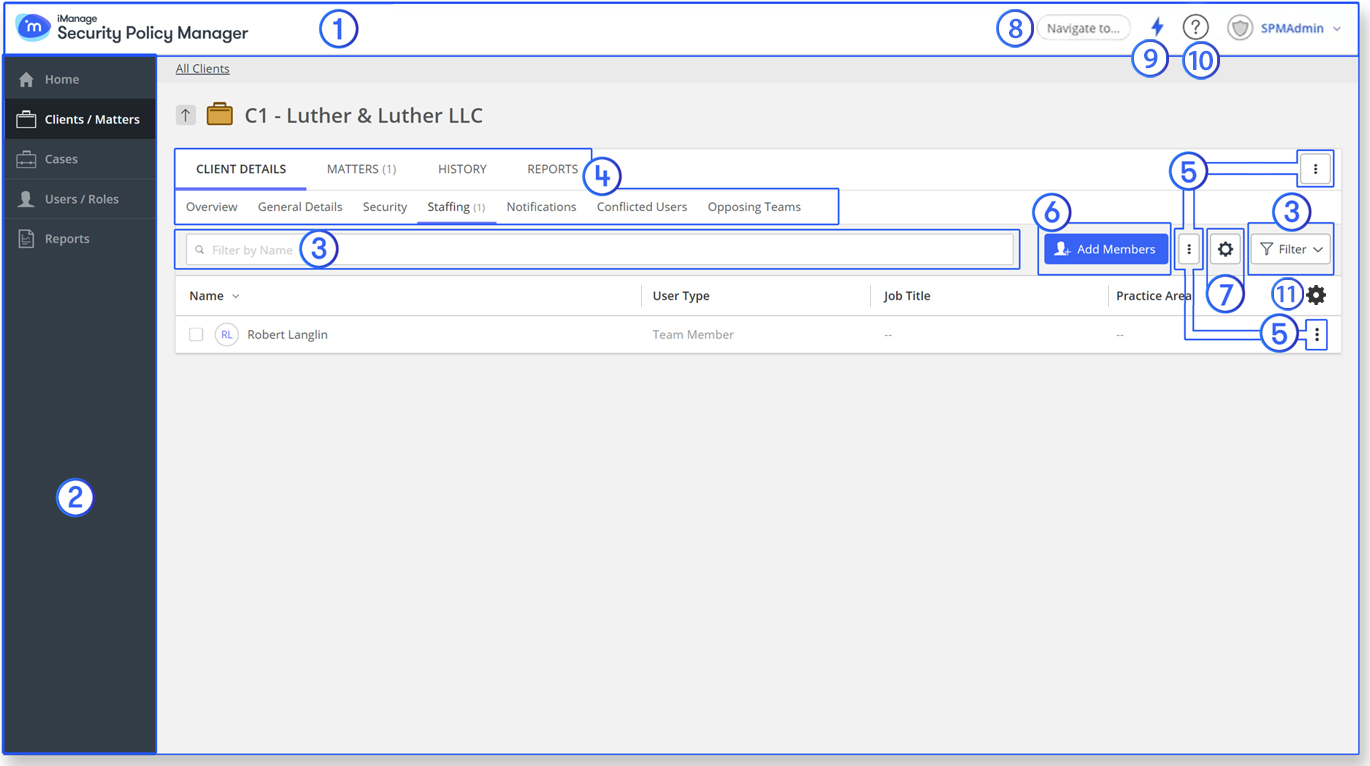
Figure: SPM Administration Console interface
NOTE:
Visibility of some interface items depends on your role. In addition, the iManage SPM Administration Console is responsive, so the arrangement of some items can differ from how they are described in this document, depending on the device you are using. All administrative functionality is, however, retained on such devices.
Table: Description of numbered UI elements
# | UI element | Description |
|---|---|---|
1 | Top banner | The top banner comprises the product logo on the left side and the common tasks that you can perform, after you sign in. Based on your defined role, the list of common tasks differ. |
2 | Left navigation pane | The left navigation pane lists the primary tabs (Home, Matters, Clients, Collections*, Cases, Opposing Team Sets*, Holds*, Users / Roles and Reports) from where you can navigate to the corresponding tasks you can perform under each tab. This left navigation pane is populated based on your user role in the iManage Security Policy Manager application. |
3 | Filters (Search Bar) | Filters are provided on certain pages, where the list of clients, matters, client/matter teams, client groups, collections, cases, and so on are populated,. The Search bar provides the ability to perform text searches. The filtering feature enables you to lock specific criteria, and use them as filters when searching and browsing content. In this way, you only work with relevant information that matches your filters. For more information, refer to Filters. |
3* | Filter pins | Filter pins (select Pin to apply) are provided in the filter drop-down menu to pin the filter to the left navigation pane. You may use this feature if you use the filtering option frequently, for ease of use. To unpin, select Unpin. |
3* | Pinnable filters | Individual, applied, filters can be pinned. For example, you can pin the responsible attorney filter to a staffing list. Example of pinned filter: For more information, refer to Pinning individual filters in Common Actions. |
4 | Tabs | Tabs (General details, Security, Opposing team sets, and so on) are provided for navigation to the respective pages/panes in the application, for your further action. |
5 | More Options buttons | The more options button () appears when you have more than one action to be performed. Selecting it displays the list of actions that you can perform, and you can choose to perform one action from among them. On some pages, options listed under the more options button are also available on row hover. For more information refer to Common Actions. |
6 | Buttons | Buttons (Save, Cancel, Back and so on) are provided to complete any action. Selecting a button ensures that the desired effect is actioned. |
7 | Rules icon | The Rules icon () is available on the Staffing page of the assets to add, view or update self-maintaining rules. |
8 | Quick Navigation | Access an asset, an opposing team set, a collection or a hold with Quick Navigation by entering the asset ID, opposing team set ID, hold ID, or collection ID respectively, in this field. Incomplete entries are applied as filters to the client list. TIP: You can access Quick Navigation instantly by pressing /, or n, on your keyboard (or other input device). |
9(a) | My Activities | My Activities displays a list of any long-running tasks initiated by the signed-in user, that are being processed in SPM, along with their start time. My Activities can be accessed at any time by selecting My Activities on the top banner. Items in the list can be sorted and filtered as required. Selecting an item in the list opens the page corresponding to that task—for example:
The progress of each task is displayed as a percentage. All items generated by the signed-in user within the last hour, including completed reports, are displayed. If there are any errors during the processing of asset security changes, these can be viewed in My Activities. When errors are present, a red dot is displayed on the My Activities symbol: |
9(b)* | What's New | You can view the latest iManage SPM features and announcements in iManage Security Policy Manager with the What's New panel. The What's Newbutton shows the number of unread What's New notifications, and selecting the button opens the panel. NOTE: This feature is available only for iManage Security Policy Manager in the Cloud. You can optionally provide feedback on each notification, for example on a new feature. All feedback, including written feedback entered in Send us your feedback, is sent directly to iManage. |
10 | Help | Select the Help icon to access the online administration manual, which provides you with information about how to use all of the functionality in iManage Security Policy Manager. |
11 | Show/Hide Columns | Select the gear icon () to adjust the visibility of header columns. This enables you to quickly access all relevant information regardless of screen size. Note that column width can be also adjusted dynamically, by dragging the handles on column headers, or double-clicking them to expand. Columns can be customized on all list pages in SPM, and your choices are remembered on next sign-in. |
*Not shown in figure.
User representation
Users in SPM are represented principally by their Full Name throughout the SPM administration console. Usernames, and email addresses when available, are also displayed with the full name.
TIP:
Username is the unique value entered by users when signing in, and can be used to help identify users in the SPM admin console.
In applicable notifications and reports also, user full name, username, and email address (when available), are displayed.
Figure: Example of a user represented in a list view
Figure: Example of a user represented in a pop-up tooltip
Common actions
The following table describes some of the common and repetitive actions that you can perform across the interface.
Action | Description |
|---|---|
Pinning individual filters | Individual, applied, filters can be pinned by selecting the pin icon. For example, you can pin the responsible attorney filter to a staffing list.
The filters that you pin are retained within the browser you are using, and between sessions, on a given device. In addition, they're applied across similar pages of a given asset type. |
Pinning the filter bar | Select the Pin icon () in the Filter menu to pin the filter bar next to the left navigation pane. To unpin it, select Unpin (). |
Applying multiple filters | You can apply more than one filter at a time to refine your search results. |
Selecting a user | Select a check box to select a user to be added. Alternatively, click a selected row to select the user. |
Deselecting a user | Clear a check box to remove the user from the selected user list. Alternatively, click a selected row to clear that selection. |
Navigating to previous page | Select the left arrow button () to navigate to the previous page. You can also use the back button on your web browser to perform this function. |
Quick Navigation | On the top navigation pane, select and enter the asset ID (including matter ID, if enabled), opposing team set ID, hold ID, or collection ID to navigate to the respective page. TIP: You can also access Quick Navigation by pressing n on your keyboard (or other input device). |
Direct access by row hover | On some pages, one-click access is available to key items by hovering on the row of the item. The hover menus available are:
|
Send an ad hoc email | Send ad hoc emails to any user in SPM that has an email address, using the Mail action. When Mail is selected from the kebab menu, the user's active mail client will launch, pre-populated with the recipients' email addresses. The Mail menu option is available throughout SPM administration console, and supports:
Mail can be sent to individual users, or a multiselected list. Example: Mail action on a matter page NOTE: When mailing a group, the email is sent to individual recipients in the group, not the group email address. When you select users that do not have email addresses, a message appears of type: "The following selected user does not have an email address:<usernames>." If over 100 email addresses are selected, SPM provides a link to copy the email addresses in semicolon separated format, for pasting into your email app. This bypasses the browser limit. |
Adjust column width and visibility | Refer to Show/Hide columns. |
Accessing the help
The Help icon on the top banner provides you with access to information that can help you make full use of iManage Security Policy Manager (SPM).
Select the Help icon to access the online administrator manual for iManage SPM.
Setting the language of SPM administration console
SPM can be displayed in American English, British English, Japanese, or alternative languages if these have been added. The language of SPM is set by the locale or language settings of the browser used to access the SPM console.
For more information about adding or customizing languages, refer to Setting the language of SPM.
Key Terminology
Term | Description |
|---|---|
Access Requests | In case of restricted security, access to a matter can be requested or provided on an ongoing basis. There are six possibilities for requesting, approving or providing access.
|
Allowed Users | Users who have access to the assets (and child assets) and are not excluded for being a conflicted user or on opposing team sets. |
Asset ID | Asset ID refers to any of Client ID, Matter ID, Client Group ID or Case ID, as applicable. Refer to Assets. |
Assets | Clients, matters, client groups, and cases are collectively referred to as "assets", or equivalently, as "items" in the documentation. |
Assistants | Assistants are users who are associated with a timekeeper to provide secretarial services or perform administrative tasks related to the timekeeper. |
Basic Team Members | When part of an asset as 'Basic Team Members', users can:
|
Candidate Users | Users who have either billed hours or performed document activity on an asset, but who are not members of asset staffing, are considered Candidate Users. |
Cases | Cases are group of matters that are sub-judice and are expected to be handled by a common team. Cases are also referred to as matter groups. A matter that has been added under a case assumes all the settings defined at the case level. When a matter is under a case, the matter settings cannot be modified. However, opposing team sets and conflicted users are configurable under matters. |
Client / Client Group Team | Client / Client Group team implies the list of users (legal representatives) who would be part of the teams working on underlying matters. Client / Client group teams are defined when adding clients / client groups into iManage Security Policy Manager. |
Client Groups | A client group comprises a group of clients that has certain commonality. For example, the clients under the client group can be serviced by a common team, the list of clients under client group could be subsidiaries of the same parent organization, and so on. A client group need not have any clients under it. However, that is only by design and not the desired functionality. When you add clients to the client group, all the matters under the client are automatically added to the client group. After a client is included in a client group, client-level settings are disabled. |
Collections | A collection comprises a set of defined policy elements, such as staffing and custom properties, that can be used to provide departmental security on an inclusionary or exclusionary basis. |
Conflicted Users | Users with conflict of interest or whom an asset administrator may not permit to be on their team, for any reason, are added as conflicted users on the asset. Conflicted users must be excluded from access to the current asset. For example, an attorney might have a conflict with a client due to previous employment history (lateral hire) or through some relationship with an employee in that company. |
Custodians | Hold custodians are users who have, or had, access to potentially relevant information in items under a hold. Refer to Holds. |
Discrepancy | A Discrepancy occurs if a user is added to the staffing of an asset but is unable to access content due to a conflict of interest, or through working in an opposing team set. TIP: You can configure notifications to be sent to specified users when discrepancies arise or are resolved. |
Excluded Systems | In the case of Restricted security, it is possible to list those systems where the policy should not be applied. In this context, a "system" is any system connected to SPM by an agent, for example, iManage Work. Excluded Systems in SPM are specified by the unique identifier (name) of the agent connecting that system to SPM. TIP: You can obtain an agent's unique identifier by viewing the Agents panel on the SPM Home Page. The unique identifier is the agent name displayed in the agent list, before any _libraryname suffix. |
Excluded Users | Users whose access to an asset is removed for being a conflicted user or on opposing team sets. |
External Users | For SPM Agents that support the use of External Users, a user designated as an External User can only see clients and matters where they are explicitly included in Staffing. An example of such a user can be a contract user. The professional services firm might not want these users to provide unhindered access to all the open assets. Such users will be able to see an asset only if included in the asset staffing. |
Floating Users | Users assigned as floating users can be assigned to staffing teams without triggering exclusions from any other opposing team sets. Secretarial users, document processors, auditors, and so on are some examples of users who can be assigned the floating user role. |
Historical Users | Users, who at a certain point in time had access to an asset, are deemed to be historical users of the asset. |
Holds | Holds comprise an item or group of items that contain information that is potentially relevant to a legal hold. SPM Holds enable definition and management of such items and their custodians, including notifications, acknowledgement, scheduled reviewed and audit. Refer to Holds. |
Included Systems | In case of matters that are either 'restricted', or 'secured by <asset>', users' access can be restricted to specific systems on a per-matter basis. Such systems to which a user has been given specific access are known as Included Systems. In this context, a "system" is any system connected to SPM by an agent, for example iManage Work. Included Systems in SPM are specified by the unique identifier (name) of the agent connecting that system to SPM. TIP: You can obtain an agent's unique identifier by viewing the Agents panel on the SPM Home Page. The unique identifier is the agent name displayed in the agent list, before any _libraryname suffix. |
Insiders | Insiders are individuals who may have had access to the asset-level information irrespective of whether they are on the asset staffing. Insiders are at two levels: permanent Insiders and matter-level Insiders.
|
Item | Clients, matters, client groups, and cases are referred to as "items". The term "item" is used equivalently with "assets" in the documentation. |
Marked as deleted | Some users or groups may be presented with transparent or strike-through formatting, and adjoining tooltip of type "This user has been marked as deleted". This indicates that such users or groups have been deleted in the import target system. While such users remain visible, all of their functionality in SPM is disabled. For more information, refer to the iManage Security Policy Manager Import and Scheduled Import Setup section in iManage Security Policy Manager Installation Guide. |
Matter Team | Matter team implies the list of users (legal representatives) who are working on a matter. Based on the security type defined for a matter under a client, the matter team is formed. If the security type is:
|
Open Security | This is an open-for-all setting. However, users working with opposing assets or conflicted users with the current asset are excluded. |
Opposing Team Sets | Staffing from the professional services firm who are working on opposing team sets with respect to the current asset team are known as opposing team sets. Staff working for these teams must be excluded from access to the current asset. At a:
|
Over the Wall Users (OTW) | These are the set of users who have access to all clients and matters in the system unless they have been specifically denied access through Conflicted users or Opposing clients and matters. |
Restricted Security | This setting restricts access to a defined set of users. The security restriction can be applied at the asset level. Authorized users are named in the client team unless the matter is individually secured. Restricted security at the parents asset (Client or Client Group) level can be either of the following:
|
Secured by Client | When the client-level security is 'Restricted', a matter under it can assume a security level that restricts matter access to users who are defined at the client level. You cannot modify the user list at the matter level. You can modify the list only at the client level. |
Security | These are the settings that define the accessibility of the assets. The setting includes configuring the list of users with access, list of users restricted from access, and so on. In iManage Security Policy Manager, client / client group / case security is classified into the following two types:
|
Support Staff | Support Staff cover secretarial staff or document processors - people who are needed to perform the work for the asset but who are not considered to be in the asset team. Support staff might not, for example, be sent notifications related to changes for the asset. Users get added as Support Staff for an asset, when they are assistants to Asset Team Members, if SPM is configured to automatically include assistants along with their Timekeepers. |
Team Members | When part of an asset as Team Members, users can:
|
Timekeepers | Timekeepers are users whose time on an asset is accounted for and are expected to be billed on that asset. |